
DNS Domain Name System
DNS : Introduction: DNS (Domain Name System) is a fundamental protocol used on the internet and local networks to translate human-readable domain names into numerical IP addresses. It plays a cruc...

DNS : Introduction: DNS (Domain Name System) is a fundamental protocol used on the internet and local networks to translate human-readable domain names into numerical IP addresses. It plays a cruc...
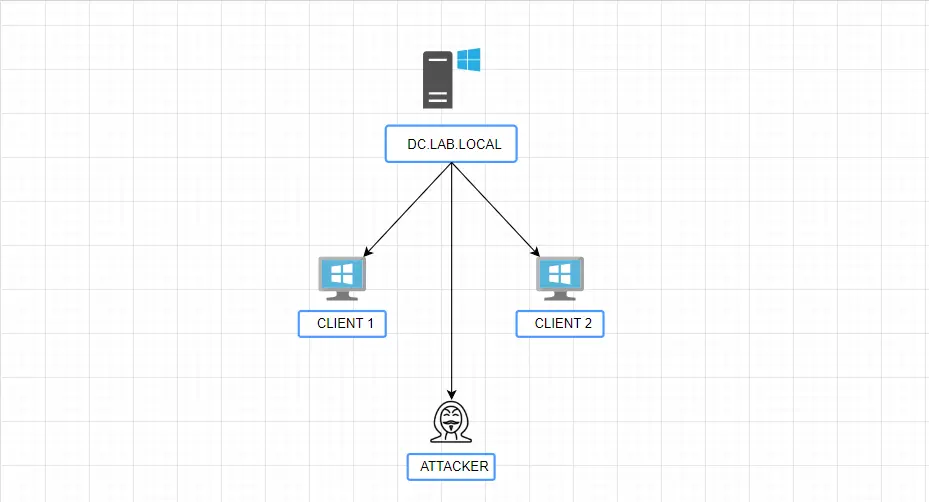
Setting Up a Windows Server for Penetration Testing with Active Directory 1. Introduction Overview of the blog's purpose : Welcome to the Active Directory Pentesting Blog, your ultimate guide fo...

Port scanning is a scanning method for determining which ports on a network device are open, whether it's a server, a router, or a regular machine. A port scanner is just a script or a program that...

Extracting saved passwords in the most popular browser is a useful and handy forensic task, as Chrome saves passwords locally in an SQLite database. However, this can be time-consuming when doing i...